What is an Open and Closed System?
A system which is connected to the network and is ready for communication is called open system.
A system which is not connected to the network and can’t be communicated with. It is called closed system.
What is Computer Networking?
A computer network is a system that connects numerous independent computers in order to share information (data) and resources.
Wireless Network: “Wireless” means without wire, media that is made up of electromagnetic waves (EM Waves) or infrared waves.
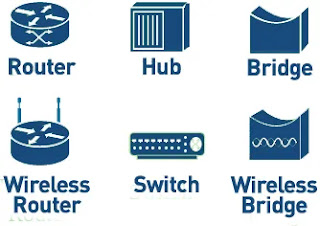
Here is the common network device list:
- Hub
- Switch
- Router
- Bridge
- Gateway
- Modem
- Repeater
- Access Point
The layout arrangement of the different devices in a network. Common examples include: Bus, Star, Mesh, Ring, and Daisy chain.
Types of area networks – LAN, MAN and WAN
- Local Area Network (LAN): A LAN is a network that covers an area of around 10 kilometers. For example, a college network or an office network. Depending upon the needs of the organization, a LAN can be a single office, building, or Campus. We can have two PCs and one printer in-home office or it can extend throughout a company and include audio and video devices. Each host in LAN has an identifier, an address that defines hists in LAN. A packet sent by the host to another host carries both the source host’s and the destination host’s address.
- Metropolitan Area Network (MAN): MAN refers to a network that covers an entire city. For example: consider the cable television network.
- Wide Area Network (WAN): WAN refers to a network that connects countries or continents. For example, the Internet allows users to access a distributed system called www from anywhere around the globe.WAN interconnects connecting devices such as switches, routers, or modems. A LAN is normally privately owned by an organization that uses it. We see two distinct examples of WANs today: point-to-point WANs and Switched WANs
The Network allows computers to connect and communicate with different computers via any medium. LAN, MAN, and WAN are the three major types of networks designed to operate over the area they cover. There are some similarities and dissimilarities between them. One of the major differences is the geographical area they cover, i.e. LAN covers the smallest area; MAN covers an area larger than LAN and WAN comprises the largest of all.
There are other types of Computer Networks also, like :
- PAN (Personal Area Network)
- SAN (Storage Area Network)
- EPN (Enterprise Private Network)
- VPN (Virtual Private Network)
What
LESSON 1
Introduction
- Computer Networking Overview
- What This Class is Not About
LESSON 2
Architecture & Principles
- A Brief History of the Internet
- Architectural Design Principles
- Packet Switching
- File Transfer
- End to End Argument Violations
LESSON 3
Switching
- Switching and Bridging
- Bootstrapping: Networking Two Hosts
- ARP: Address Resolution Protocol
- Interconnecting LANs with Hubs
- Switches: Traffic Isolation
- Spanning Tree
- Switches vs. Routers
- Buffer Sizing for a TCP Sender
LESSON 4
Routing
- Internet Routing
- Intra-AS Topology
- Distance-Vector Routing
- Link State Routing
- Interdomain Routing
- IGP vs. iBGP
- BGP Route Selection
- Multiple Exit Discriminator (MEI)
- Interdomain Routing Business Models
LESSON 5
Naming, Addressing & Forwarding
- IP Addressing
- Pre-1994: “Classful” Addressing
- IP Address Allocation
- Classless Interdomain Routing (CIDR)
- Multihoming Frustrates Aggregation
- Address Lookup Using Tries
- Memory Efficiency and Fast Lookup
- Alternatives to LPM with Tries
- NAT and IPv6
- Network Address Translation (NAT)
LESSON 6
Router Design Basics
- Router Design
- Basic Router Architecture
- Decision: Crossbar Switching
- Switching Algorithm: Maximal Matching
- Head of Line Blocking
- Scheduling and Fairness
- Max-Min Fairness
LESSON 7
Domain Name System (DNS)
- Record Types
- Examples (using “dig”)
- Lookup IP Address
LESSON 8
Congestion Control & Streaming
- Congestion Control
- AIMD (TCP Congestion Control)
- Data Centers & TCP “Incast”
- Barrier Synchronization & Idle Time
- Multimedia & Streaming
- Digitizing Audio & Video
- Streaming Video
- Skype
LESSON 9
Rate Limiting and Traffic Shaping
- Traffic Classification & Shaping
- Source Classification
- Leaky Bucket Traffic Shaping
- (r, t) Traffic Shaping
- Shaping Bursty Traffic Patterns
- Power Boost
- Effects on Latency
- Buffer Bloat
- Packet Monitoring
LESSON 10
Content Distribution
- The Web and Caching
- HTTP Requests
- Persistent Connections
- Content Distribution Networks (CDNs)
- Server Selection
- Content Routing
- Bit Torrent
- Solution to Freeriding: “Choking”
- Distributed Hash Tables
- Consistent Hashing
LESSON 12
Traffic Engineering
- Traffic Engineering Overview
- Interdomain Traffic Engineering
- Measuring, Modeling and Controlling Traffic
- Link Utilization Function
- BGP in Interdomain Traffic Engineering
- Multipath Routing
- Data Center Networking
- Valiant Load Balance
- Jellyfish Data Center Topology
LESSON 13
Network Security
- Internet is Insecure
- Resource Exhaustion
- Routing Security
- Origin and Path Authentication
- DNS Security
- DNS Cache Poisoning
LESSON 14
Internet Worms
- Viruses and Internet Worms
- Internet Worm Lifecyle
- First Worm: “Morris” Worm
- Worm Outbreaks in Detail
- Modeling Fast-Spreading Worms
LESSON 15
Spam
- Spam
- IP Blacklisting
LESSON 16
Denial of Service (DoS) Attacks
- TCP 3-Way Handshake
- Inferring Denial of Service Activity using Backscatter
- Automated DoS Attack Mitigation
- MTPCP




0 Comments
If you have any doubts. Please let me know